Remote IoT device SSH has become an essential tool for businesses and individuals seeking to manage and monitor their Internet of Things (IoT) devices from anywhere in the world. As the demand for remote access and management continues to grow, finding the best remote IoT device SSH solution is more critical than ever. This technology not only enhances efficiency but also ensures security in managing IoT networks.
With the rise of smart homes, smart cities, and industrial automation, the need for secure remote access to IoT devices has skyrocketed. Whether you're a network administrator, a developer, or an enthusiast, understanding the best practices and tools for remote IoT device SSH can significantly improve your operations.
In this comprehensive guide, we will explore everything you need to know about remote IoT device SSH, from its benefits and challenges to the top solutions available in the market. By the end of this article, you'll have a clear understanding of how to choose the best remote IoT device SSH solution for your needs.
Read also:Mia Khalifa A Comprehensive Look Into Her Career Life And Achievements
Table of Contents
- Introduction to Remote IoT Device SSH
- Benefits of Using Remote IoT Device SSH
- Challenges in Implementing Remote IoT Device SSH
- Top Remote IoT Device SSH Solutions
- Criteria for Choosing the Best Remote IoT Device SSH
- Enhancing Security in Remote IoT Device SSH
- Comparison of Popular Remote IoT Device SSH Tools
- How to Set Up Remote IoT Device SSH
- The Future of Remote IoT Device SSH
- Conclusion and Call to Action
Introduction to Remote IoT Device SSH
Remote IoT device SSH is a powerful technology that allows users to securely access and manage IoT devices from a remote location. SSH, or Secure Shell, is a cryptographic network protocol that provides secure communication over unsecured networks. By leveraging SSH, users can control and monitor IoT devices without being physically present.
SSH ensures that data transmitted between devices is encrypted, making it difficult for unauthorized users to intercept or manipulate the information. This is particularly important in IoT environments, where devices often communicate sensitive data.
As the number of connected devices continues to grow, remote IoT device SSH has become a necessity rather than a luxury. It enables businesses to streamline their operations, reduce downtime, and improve overall efficiency.
Benefits of Using Remote IoT Device SSH
Implementing remote IoT device SSH offers numerous advantages for both individuals and organizations. Here are some of the key benefits:
Enhanced Security
SSH provides robust encryption and authentication mechanisms, ensuring that data transmitted between devices remains secure. This is crucial in protecting sensitive information from cyber threats.
Increased Efficiency
With remote IoT device SSH, users can manage multiple devices simultaneously from a single location. This eliminates the need for physical presence, saving time and resources.
Read also:Emory Tate Height A Comprehensive Look Into The Life And Career Of A Chess Legend
Cost Savings
By reducing the need for on-site visits, remote IoT device SSH can significantly lower operational costs. Businesses can allocate their resources more effectively, focusing on strategic initiatives rather than routine maintenance tasks.
Additionally, remote access allows for faster troubleshooting and issue resolution, minimizing downtime and potential revenue losses.
Challenges in Implementing Remote IoT Device SSH
While remote IoT device SSH offers numerous benefits, there are also challenges to consider. Understanding these challenges can help organizations implement the technology more effectively:
Security Risks
Although SSH provides strong encryption, it is not immune to attacks. Hackers can exploit vulnerabilities in the protocol or use brute-force attacks to gain unauthorized access. It is essential to implement additional security measures, such as firewalls and intrusion detection systems, to mitigate these risks.
Complexity
Setting up and managing remote IoT device SSH can be complex, especially for organizations with limited technical expertise. Proper training and support are necessary to ensure successful implementation.
Compatibility Issues
Not all IoT devices are compatible with SSH. Organizations must ensure that their devices support SSH before implementing the technology. In some cases, firmware updates or additional hardware may be required to enable SSH functionality.
Top Remote IoT Device SSH Solutions
There are several remote IoT device SSH solutions available in the market, each with its own strengths and weaknesses. Here are some of the top options:
Tailscale
Tailscale is a popular SSH-based solution that simplifies remote access to IoT devices. It offers seamless integration with various platforms and provides robust security features, including end-to-end encryption and zero-trust architecture.
Ngrok
Ngrok is another widely used tool for remote IoT device SSH. It allows users to create secure tunnels to access devices behind firewalls or NATs. Ngrok is easy to set up and offers both free and paid plans, making it accessible for individuals and businesses alike.
Cloudflare Tunnel
Cloudflare Tunnel is a secure and scalable solution for remote IoT device SSH. It provides fast and reliable connections while ensuring data privacy and security. Cloudflare Tunnel is particularly well-suited for large-scale deployments and enterprise environments.
Criteria for Choosing the Best Remote IoT Device SSH
When selecting a remote IoT device SSH solution, it is important to consider the following criteria:
- Security: Ensure the solution offers robust encryption and authentication mechanisms.
- Compatibility: Verify that the solution is compatible with your IoT devices and platforms.
- Scalability: Choose a solution that can grow with your needs and accommodate future expansion.
- Usability: Opt for a solution that is easy to set up and manage, even for non-technical users.
- Support: Look for a provider that offers reliable customer support and resources.
Enhancing Security in Remote IoT Device SSH
Security is a top priority when implementing remote IoT device SSH. Here are some best practices to enhance security:
Use Strong Passwords
Weak passwords are a common vulnerability in SSH implementations. Use strong, complex passwords and consider enabling two-factor authentication (2FA) for an extra layer of protection.
Regularly Update Software
Keep your SSH software and firmware up to date to address any security vulnerabilities. Regular updates ensure that your system is protected against the latest threats.
Monitor Activity
Implement logging and monitoring tools to track SSH activity and detect any suspicious behavior. This can help prevent unauthorized access and ensure the integrity of your IoT network.
Comparison of Popular Remote IoT Device SSH Tools
Below is a comparison of some popular remote IoT device SSH tools based on key criteria:
| Tool | Security | Compatibility | Scalability | Usability |
|---|---|---|---|---|
| Tailscale | High | Excellent | Good | Easy |
| Ngrok | Medium | Good | Good | Easy |
| Cloudflare Tunnel | High | Excellent | Excellent | Advanced |
How to Set Up Remote IoT Device SSH
Setting up remote IoT device SSH involves several steps. Here's a step-by-step guide:
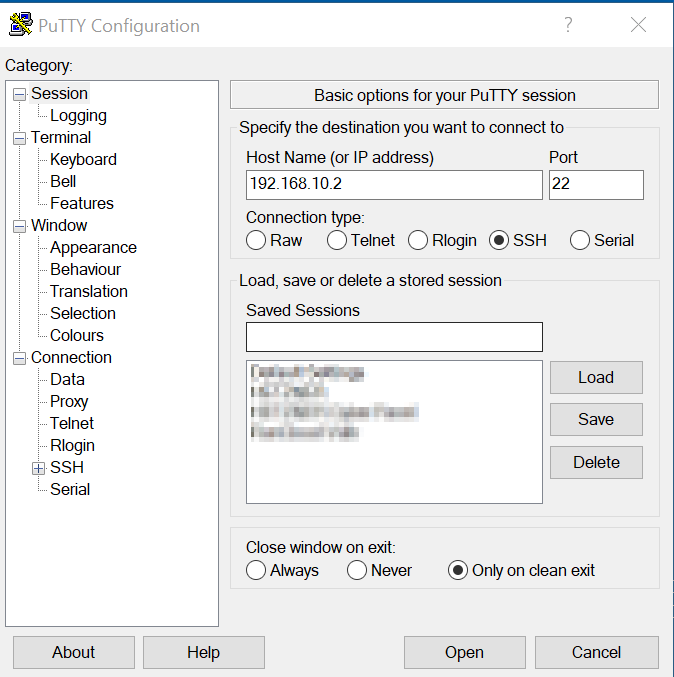
- Install SSH Client: Install an SSH client on your local machine, such as PuTTY for Windows or the built-in terminal for macOS and Linux.
- Enable SSH on IoT Device: Ensure that SSH is enabled on your IoT device. This may involve modifying the device's settings or updating its firmware.
- Configure Firewall: Configure your firewall to allow incoming SSH connections on the appropriate port (usually port 22).
- Test Connection: Test the SSH connection by entering the device's IP address and credentials in your SSH client.
The Future of Remote IoT Device SSH
As IoT continues to evolve, remote IoT device SSH will play an increasingly important role in managing and securing connected devices. Emerging technologies such as quantum encryption and artificial intelligence are expected to further enhance the security and functionality of SSH.
Additionally, the growing adoption of 5G networks will enable faster and more reliable remote access to IoT devices, opening up new possibilities for businesses and individuals alike.
Conclusion and Call to Action
In conclusion, remote IoT device SSH is a vital technology for anyone looking to manage and secure their IoT devices from a distance. By understanding the benefits, challenges, and best practices associated with remote IoT device SSH, you can make informed decisions about implementing this technology in your operations.
We encourage you to share your thoughts and experiences in the comments section below. Have you used any of the tools mentioned in this article? What challenges have you faced in implementing remote IoT device SSH? Let us know, and don't forget to explore our other articles for more insights into IoT and related technologies.
References: