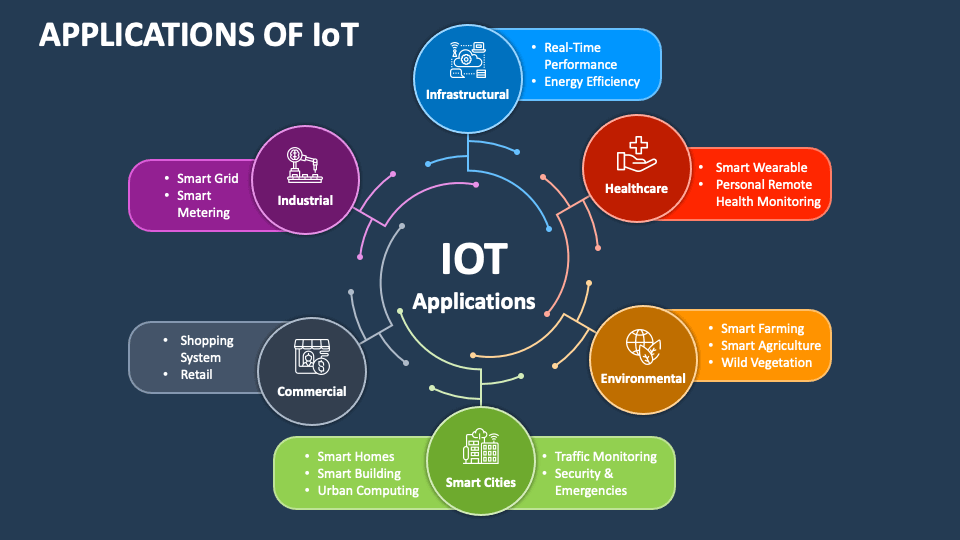
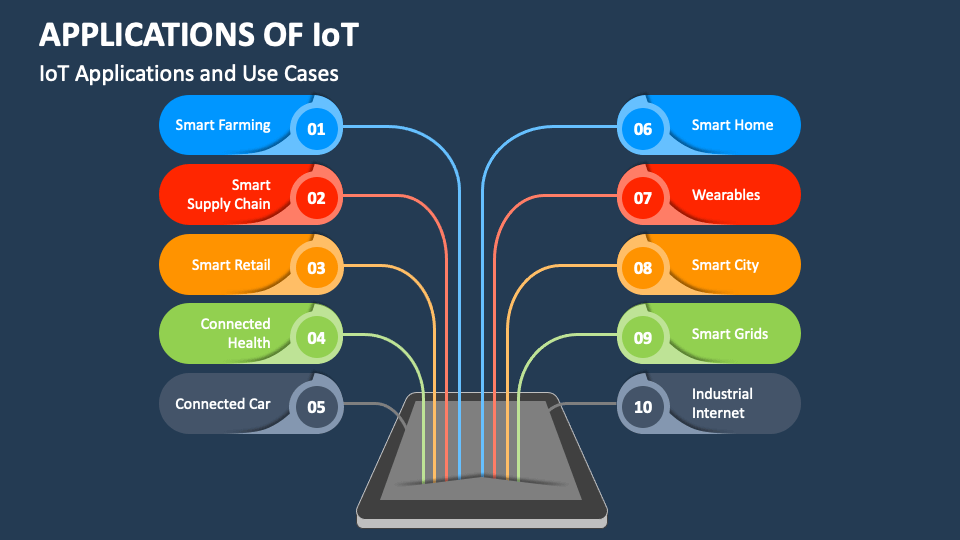
In the rapidly evolving world of technology, SSH IoT applications have become increasingly important. These applications play a critical role in enabling secure communication between Internet of Things (IoT) devices. As IoT continues to expand, understanding SSH and its applications is essential for ensuring secure and reliable connectivity.
SSH, or Secure Shell, is a cryptographic protocol used to secure network services over an unsecured network. In the context of IoT, SSH ensures that data transmitted between devices remains encrypted and protected from unauthorized access. This is particularly crucial as IoT devices are often deployed in environments where security risks are high.
This article aims to provide a detailed overview of SSH IoT applications, their benefits, challenges, and implementation strategies. By the end of this guide, readers will have a comprehensive understanding of how SSH enhances IoT security and its practical applications in various industries.
Read also:Putting Salt Under Tongue A Comprehensive Guide To Benefits Risks And Expert Insights
Table of Contents
- What is SSH?
- SSH in IoT: An Overview
- Benefits of SSH IoT Applications
- Common SSH IoT Applications
- Challenges in SSH IoT Implementation
- Best Practices for SSH IoT Deployment
- Security Considerations for SSH IoT
- Industry Use Cases of SSH IoT
- Future Trends in SSH IoT
- Conclusion
What is SSH?
SSH, or Secure Shell, is a network protocol designed to provide secure communication over unsecured networks. Developed in the late 1990s, SSH has become a standard for securing remote access to computer systems. It uses encryption to protect data integrity and confidentiality, making it an ideal solution for IoT environments where security is paramount.
SSH operates on a client-server model, where a client initiates a connection to a server. The protocol supports authentication mechanisms, including password-based and public key authentication, ensuring that only authorized users can access the system.
One of the key features of SSH is its ability to create a secure tunnel for data transmission. This tunnel encrypts all data passing through it, protecting it from interception and tampering. In the context of IoT, this feature is particularly valuable, as it ensures that sensitive information exchanged between devices remains secure.
SSH in IoT: An Overview
The Internet of Things (IoT) refers to a network of interconnected devices capable of collecting and exchanging data. These devices range from simple sensors to complex industrial machinery, all requiring secure communication to function effectively. SSH IoT applications address this need by providing a secure framework for data exchange.
Why SSH is Critical for IoT
IoT devices are often deployed in environments where security risks are high. Without proper security measures, these devices can become vulnerable to attacks, leading to data breaches and system failures. SSH mitigates these risks by:
- Encrypting data during transmission.
- Providing strong authentication mechanisms.
- Ensuring data integrity through cryptographic hashing.
By implementing SSH in IoT, organizations can significantly enhance the security of their networks and protect sensitive information from unauthorized access.
Read also:Ivory Hills Japan Where Is It And What Makes It A Mustvisit Destination
Benefits of SSH IoT Applications
SSH IoT applications offer numerous advantages that make them an attractive solution for securing IoT networks. Below are some of the key benefits:
Enhanced Security
SSH ensures that data transmitted between IoT devices remains encrypted and protected from interception. This is achieved through robust encryption algorithms and secure authentication mechanisms.
Improved Reliability
By securing communication channels, SSH reduces the risk of data loss and system failures. This leads to more reliable IoT networks that can operate efficiently even in challenging environments.
Scalability
SSH is highly scalable, making it suitable for use in large-scale IoT deployments. Its ability to handle multiple connections simultaneously ensures that it can support growing networks without compromising performance.
Common SSH IoT Applications
SSH IoT applications are used in a variety of industries to secure communication between devices. Some of the most common applications include:
Remote Device Management
SSH enables secure remote access to IoT devices, allowing administrators to manage and configure them from a distance. This is particularly useful in industries such as manufacturing, where devices are often located in remote locations.
Data Encryption
SSH provides end-to-end encryption for data transmitted between IoT devices, ensuring that sensitive information remains protected from unauthorized access.
Network Monitoring
SSH can be used to monitor IoT networks in real-time, providing insights into device performance and network health. This helps organizations identify and address issues before they escalate into larger problems.
Challenges in SSH IoT Implementation
While SSH IoT applications offer numerous benefits, their implementation can pose challenges. Some of the most common challenges include:
Resource Constraints
Many IoT devices have limited processing power and memory, making it difficult to implement complex encryption algorithms. This requires careful optimization to ensure that SSH can be deployed effectively on these devices.
Key Management
Managing SSH keys across a large number of IoT devices can be challenging. Organizations must implement robust key management practices to ensure that keys are securely stored and rotated as needed.
Compatibility Issues
Not all IoT devices are compatible with SSH, requiring organizations to develop custom solutions to integrate these devices into their networks. This can increase development time and costs.
Best Practices for SSH IoT Deployment
To ensure successful deployment of SSH IoT applications, organizations should follow best practices that address common challenges and maximize security. Some of these practices include:
Use Strong Authentication
Implementing strong authentication mechanisms, such as public key authentication, helps prevent unauthorized access to IoT devices.
Regularly Update Keys
Regularly updating SSH keys ensures that compromised keys are replaced promptly, reducing the risk of security breaches.
Monitor Network Activity
Continuous monitoring of network activity allows organizations to detect and respond to suspicious behavior quickly, enhancing overall network security.
Security Considerations for SSH IoT
Securing SSH IoT applications requires a comprehensive approach that addresses potential vulnerabilities. Below are some key security considerations:
Vulnerability Management
Regularly updating SSH software and addressing known vulnerabilities helps protect against attacks that exploit these weaknesses.
Access Control
Implementing strict access control policies ensures that only authorized users can access IoT devices and networks.
Data Protection
Using strong encryption algorithms and secure protocols ensures that sensitive data remains protected during transmission and storage.
Industry Use Cases of SSH IoT
SSH IoT applications are used in a variety of industries to secure communication between devices. Below are some examples of how SSH is applied in different sectors:
Healthcare
In healthcare, SSH is used to secure communication between medical devices and systems, ensuring that patient data remains confidential and protected from unauthorized access.
Manufacturing
In manufacturing, SSH is used to secure remote access to industrial control systems, enabling efficient monitoring and management of production processes.
Transportation
In the transportation industry, SSH is used to secure communication between vehicles and infrastructure, enhancing safety and efficiency in transportation systems.
Future Trends in SSH IoT
As IoT continues to evolve, SSH IoT applications are expected to play an increasingly important role in securing these networks. Some of the key trends to watch include:
Quantum-Resistant Encryption
With the advent of quantum computing, organizations are exploring quantum-resistant encryption algorithms to ensure long-term security of IoT networks.
Artificial Intelligence Integration
Integrating AI into SSH IoT applications can enhance threat detection and response capabilities, enabling more proactive security measures.
Edge Computing
Edge computing, which involves processing data closer to the source, is expected to become more prevalent in IoT networks. SSH will play a critical role in securing these distributed systems.
Conclusion
In conclusion, SSH IoT applications are essential for securing communication between IoT devices. By providing robust encryption, strong authentication, and reliable data transmission, SSH enhances the security and reliability of IoT networks. While challenges exist in implementing SSH IoT applications, following best practices and addressing security considerations can help organizations overcome these obstacles.
We encourage readers to explore SSH IoT applications further and consider implementing them in their own networks. For more information on SSH and IoT security, please leave a comment or share this article with your network. Additionally, feel free to explore other articles on our site for more insights into the world of technology and security.